Amazon CloudWatch Alarm failed to execute Action and invoke AWS Lambda Function
Using Amazon CloudWatch Alarms system engineers and cloud developers can automate responses to anomalies and responses to different workloads on their cloud resources. In this AWS guide, I want to share how cloud professionals can ensure that a specific AWS Lambda function is executed automatically in response once their Amazon CloudWatch alarm is activated or changed to alarm state.
Recently, I created an alarm using Amazon CloudWatch metrics on CloudWatch dashboard for my Amazon DocumentDB cluster. Using the actions associated with the CloudWatch Alarm, I planned to trigger an AWS Lambda function whenever my DocumentDB cluster reader node instance experiences a high CPU usage beyond the threshold that I defined.
During my tests on the CloudWatch Alarm, I realized that the Lambda function is not triggered.
When I checked the History tab of the CloudWatch Alarm, I realized that although the action is triggered it failed to invoke the AWS Lambda function.
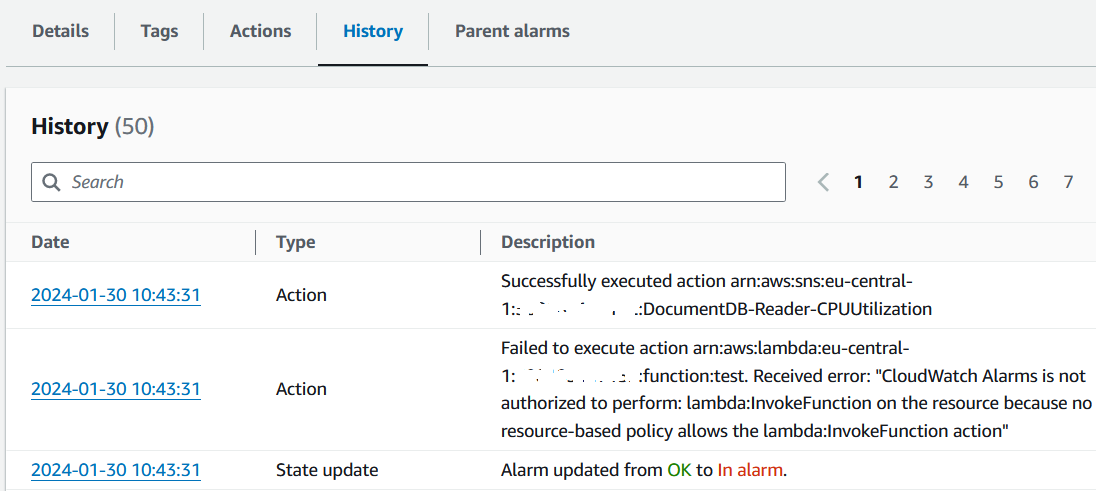
Below is the error text explaining the reason of the unsuccessful action to trigger the targeted AWS Lambda function
Failed to execute action arn:aws:lambda:eu-central-1:111122223333:function:test. Received error: "CloudWatch Alarms is not authorized to perform: lambda:InvokeFunction on the resource because no resource-based policy allows the lambda:InvokeFunction action"
This execution error is caused because Amazon CloudWatch service does not have the required permission to invoke the specified AWS Lambda function.
Unfortunately, neither of the AWS services; AWS CloudWatch Alarms or AWS Lambda functions does not provide a user interface (UI) on AWS Management Console to configure the permissions from one service resource to other. Although AWS Lambda function enables policy creation and attachment via UI for Amazon CloudWatch Logs, CloudWatch Alarms cannot be used for policies generated via AWS Management Console for Lambda functions.
Please review the official documentation published at URL Using Amazon CloudWatch alarms and Lambda alarm actions
In the user guide provided by AWS, executing below AWS CLI command is one of the suggested solutions to enable Amazon CloudWatch Alarm to invoke an AWS Lambda function successfully.
aws lambda add-permission \
--function-name my-lambda-function-name \
--statement-id AlarmAction \
--action 'lambda:InvokeFunction' \
--principal lambda.alarms.cloudwatch.amazonaws.com \
--source-account 111122223333 \
--source-arn arn:aws:cloudwatch:us-east-1:111122223333:alarm:alarm-name
I replaced the account number, Lambda function name and CloudWatch alarm name in above AWS CLI command and executed in my development environment as follows.
aws lambda add-permission --function-name myKodyazLambdaFunction --statement-id AlarmAction --action 'lambda:InvokeFunction' --principal lambda.alarms.cloudwatch.amazonaws.com --source-account 188188188188 --source-arn "arn:aws:cloudwatch:eu-central-1:188188188188:alarm:High CPU Utilization for DocumentDB Reader"
After I executed the above AWS CLI command to grant permission to Amazon CloudWatch alarm on the related AWS Lambda function, I could see that next time the alarm successfully executed the action and called that particular AWS Lambda function.
